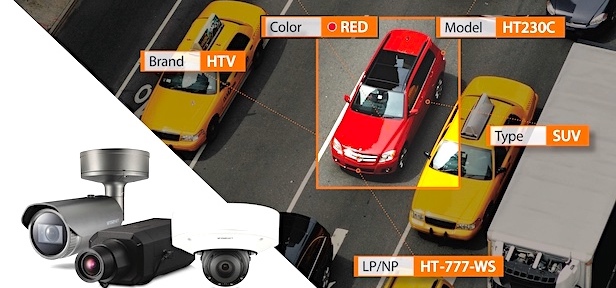
Do not have nightmares in your security system!

Security Precautions for Security Systems
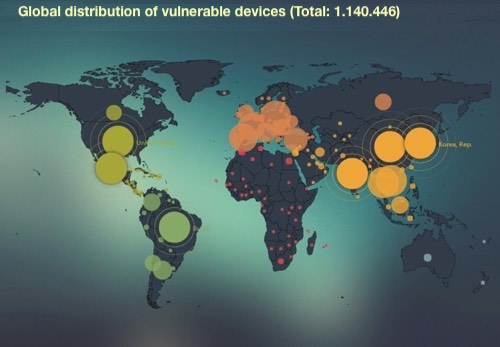
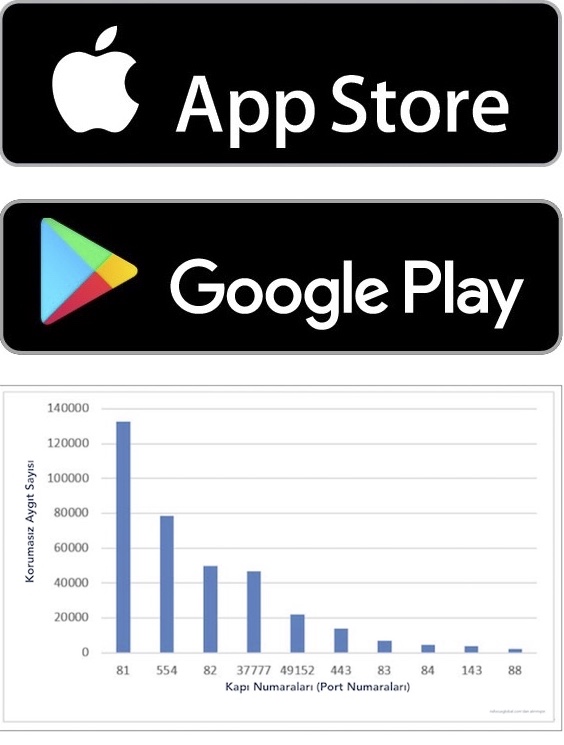
Manufacturers use specific standards and information when designing new models. However, the gaps of this information are resolved by malicious people over time. The result reveals the map above. It shows the list of recorders and IP cameras that have been hacked * as a result of one of the world's major manufacturers' network vulnerabilities. If you want to see the original and interactive version of the map, you should contact us.
This map was created by the study of a web site working on the security of network camera systems. This study is an example of limited resources.
*The map was prepared in December 2017.
What is Vulnerability?
A vulnerability in computer-based systems is the vulnerability that causes an attacker to enter the system. Vulnerabilities are the intersection of three elements:
I) SYSTEM SENSITIVITY OR DEFECT,
II) DEFICIENCY ACCESS
III) AGGRESSIVE FEATURE FOR BENEFIT.
To exploit the vulnerability, an attacker must have at least one valid tool or technique that can be attributed to system vulnerability. This framework is also known as vulnerability attack surface.
Vulnerability management is a cyclical application of vulnerability identification, classification, correction and mitigation.
What is the Importance of Security Systems?
Today's electronic security technologies work entirely on computer networks (even older analog systems have an interface that connects to computer networks).
- In particular, camera systems are open to external networks due to remote monitoring and control requirements.
- The communication requirements of the card pass systems in companies operating in multinational or in more than one city may also necessitate the opening of the systems on the internet.
- The temptation to control alarm systems via smartphones is pushing manufacturers towards cloud-based systems. In this case, it means that the alarm system is connected to the internet.
- The network-based applications simply summarized above provide an interface for anyone who can detect the IP address or dynamic DNS connection of the systems on the Internet. In order to detect gaps in the systems, these interfaces are attacked from many layers, from automated software to those who work for individual enthusiasm.
How do these vulnerabilities occur?
Vulnerabilities can occur in multiple stages.
![]() First Stage: Production
First Stage: Production
When applying standards to their systems, manufacturers avoid economic pressures, the lack of use of sufficiently experienced software developers, and sometimes avoid taking certain measures, considering that the target audience does not care. They do not create a security policy in order to ensure that every detail of the systems that are considered in the production stage will function properly in future periods and do not risk spending money for this. For example, the lack of a restriction on the passwords to be used, forcing users to complex password structure emerges as a deficiency of the manufacturer. As a result, the map above can appear.
 Step Two: Installation
Step Two: Installation
The reasons such as the lack of training of the installers, the lack of security measures in the devices to be connected to the internet, or the lack of a security policy of the manufacturer using the products leave the devices vulnerable. In particular, systems installed by unauthorized and uninformed persons are left with factory values. The lack of information and training on how to use the system safely is another element.
![]() Step Three: Use
Step Three: Use
Factors such as the fact that the users do not investigate the security issues when choosing the systems, the preference of inexperienced people to make the installation cheaper, the need to avoid the use of passwords, and the subsequent neglect of the policies applied at the beginning are the security vulnerabilities created by the user.
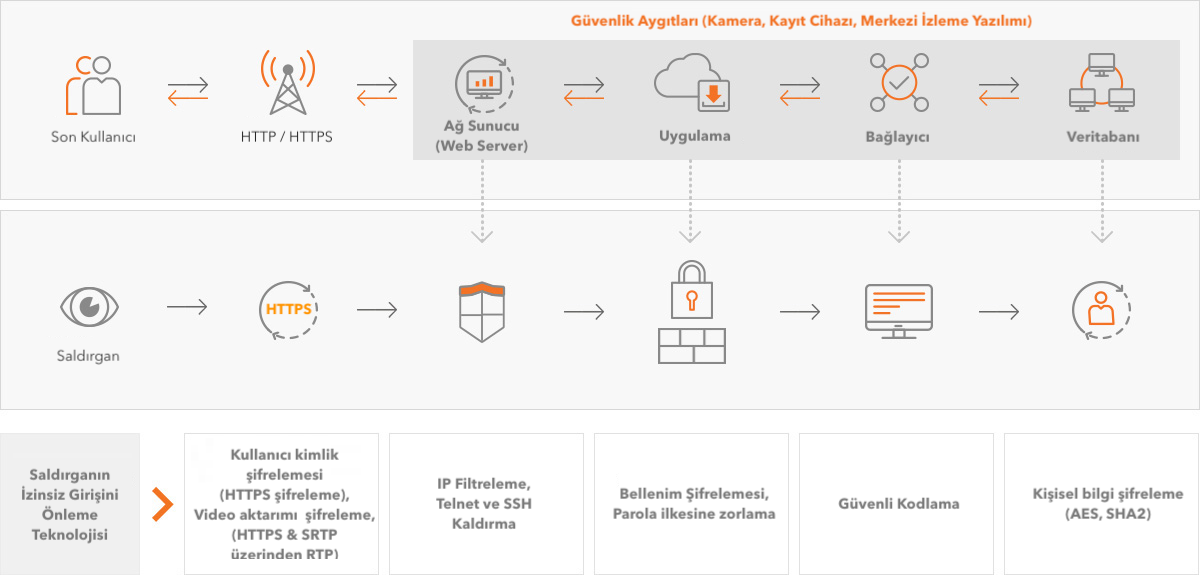
As a result, a security policy needs to be developed at all stages in which a security system is made available to the end user. It is the result of security policy that Hanwha Techwin (Samsung), who is aware of this situation, does not have a map as above. The following describes the structure of the security policy for Wisenet (Hanwha Techwin) products.

Manufacturer Safety Principles:
Latest Network Security Technologies for Protecting User Information and Systems
Our products protect systems and user information through the following state-of-the-art security technologies: - HTTPS protocol and custom certificate features to protect user authentication information (user ID / password). - RTSP-over-HTTPS tunneling and data transmission using the SRTP video encryption protocol for protection of user video information. - Eliminate vulnerabilities and bypassing bypasses through administrator rights to prevent IP filtering and unauthorized device access through the firewall. - Continuous monitoring to prevent new vulnerabilities. - Designed to protect systems from external attacks. The latest security technologies on multiple security devices are the methods we use to protect against unauthorized security bypass, user authentication, and image retrieval in each product component.
-


Protecting User Credentials
-


Protecting User Video Data
-

Protecting User Credentials
The password policy of network security products has been accepted as secure by many salespersons with its structure that can prevent authentication and information leaks caused by user error or carelessness and minimizes the security risk.


SECURITURK ™ Security Policies:
Briefly, it can be summarized as follows:
- Determining the needs of the user, revealing the shortcomings
- Fully implement all safety tools provided by the manufacturer¹
- Ensure that the principle to be applied is not punctured in any way
- Completing or reporting new firmware and software updates as soon as possible
- Ensuring safety in time until any subsequent risks are eliminated.
- Installing closed systems when possible
- Custom door policy application
¹The following security tools are our priority.
- Supporting the system with Open Source Certificates as needed
- Provide IEEE 802.1x port-based access control as needed
- Use IP filtering if appropriate for the project
- Set up a system-specific virtual private network configuration if appropriate for the project

End User Recommendation:
- Never buy or use products manufactured under the stairs.
- Do not accept unfamiliar products. Check the products you purchase through the manufacturers' websites.
- Do not buy if you do not have an internet site.
- Be sure to download the software you use from the manufacturer's websites.
- Be sure to download apps from the app store recommended by the respective phone / tablet manufacturer.
- Never work with companies that have not set a safety policy.
- Ask your installer to set the system ports to a non-factory value.
- Check your security system logs.
- Do not opt for logging security systems that can be deleted.
- Do not choose systems that allow deleting a record.
- Always check if your systems have a disk health indicator.
- Do not ignore status messages or warning icons.
- Always keep the administrator password. Do not use the administrator password continuously. If necessary, define a special password for yourself and use it.
- Never use your system with the factory password. Do not allow it to be used.
- Change your passwords periodically.
- Keep your computers and phones up to date.
- Work with installers who not only install the product but also support you at every stage.
- Definitely use unique passwords. Your passwords should be 8 characters or more. Let your password be a combination of uppercase, lowercase letters, numbers and special characters.
- If you do not need to, disconnect your devices from the network or unplug the cable.
- If you have any reason to suspect that your device has been entered, ask your installer for help.
- When destroying your devices, be sure to destroy your records.
- Change your passwords when security personnel change.
- Do not allow unauthorized persons to modify your system, even if you are supervised.
- If you need to reset the modem that provides your Internet connection, then ask your security company to reinstall it.